
reader comments
42 with 36 posters participating
IT and software development firm Globant said in a statement Wednesday that it experienced a network breach. The statement appeared to confirm claims made by Lapsus$, a group that has successfully compromised Microsoft, Nvidia, Okta, and other victims in recent weeks.
Lapsus$ is a relative newcomer to the data-extortion scene. While the group’s tactics and procedures lack sophistication, members largely believed to be young and technically immature make up for it with persistence. Gang members were rumored to be among seven individuals arrested last week by London police.
Not dead yet
A leak Tuesday on the Lapsus$ Telegram channel included data the group said came from a recent hack on Globant, raising questions about precisely what relationship the suspects, aged 16 to 21, had with Lapsus$. Recently, the FBI sought public assistance in tracking down the group.
London police don’t appear to have explicitly said the suspects were members of Lapsus$, “but, assuming [the suspects] are, we still don’t know how many other individuals are associated with the operation or where they may be based,” Brett Callow, a threat analyst with security firm Emsisoft, wrote in a private message. “For example, at least one of the members appears to be a native speaker—or, more accurately, writer—of Brazilian Portuguese.”
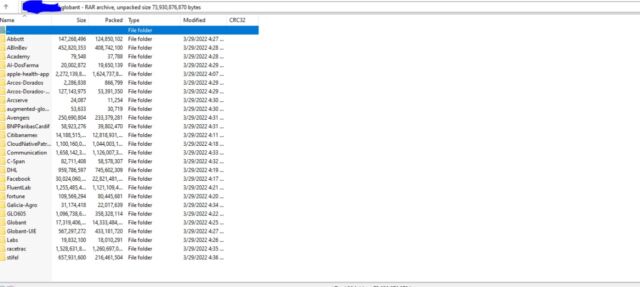
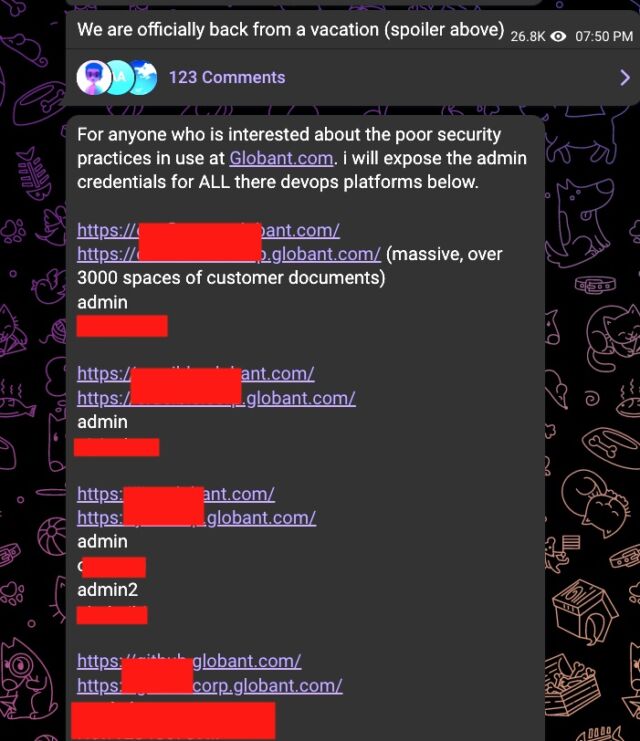
The Telegram post included a screenshot of data purportedly taken from Luxembourg-based Globant, which operates in 18 countries and has more than 23,500 employees. Folders for one of the purportedly stolen data caches had names like “apple-health-app,” “Facebook,” “C-SPAN,” and “DHL.” Another post on the same channel purported to show login credentials, many with weak passwords, for some of the servers Globant used to store the data.
Code repository breached by script kiddies
“We have recently detected that a limited section of our company’s code repository has been subject to unauthorized access,” company officials wrote in a statement. “We have activated our security protocols and are conducting an exhaustive investigation.”
So far, the statement said, the investigators believe the stolen data was “limited to certain source code and project-related documentation for a very limited number of clients.” The current probe has yet to find evidence that other data or systems were breached.
Company representatives declined to answer questions asking when the breach occurred, if the data leaked was genuine, and if anyone has approached Globant demanding a ransom.
Last week, KrebsOnSecurity and Bloomberg reported that a core Lapsus$ member is a 16-year-old living in Oxford, England. A day later, London police said that at least one of the hacking suspects they arrested was 16 years old.
Lapsus$ employs a host of unsophisticated methods to successfully breach its victims. To bypass some targets’s multifactor-authentication protections, for example, members who obtained passwords would periodically attempt logging in to the affected accounts, a technique known as MFA prompt bombing. In many cases, prompts can be delivered through a regular phone call.
“No limit is placed on the amount of calls that can be made,” a Lapsus$ member recently wrote. “Call the employee 100 times at 1 am while he is trying to sleep, and he will more than likely accept it. Once the employee accepts the initial call, you can access the MFA enrollment portal and enroll another device.”
Other techniques involved SIM swaps and social engineering. Lapsus$ is not above bribery either; once an organization is targeted, the group goes after its customers and employees of its contractors.
The continuing activity of Lapsus$ is yet another testament to the group’s resilience. While organizations frequently focus on defending against zero-day exploits and other types of advanced threats, Lapsus$ should serve as a reminder that less esoteric hacking methods are often easier and just as effective.



