A few days after the Capitol insurrection last January, the FBI got two tips identifying an Ohio man named Walter Messer as a participant, and both cited his social media posts about being there. To verify those tips, the FBI turned to three companies that held a large amount of damning evidence against Messer, simply as a result of his normal use of their services: AT&T, Facebook, and Google.
AT&T gave the FBI Messer’s telephone number and a list of cell sites he used, including one that covered the US Capitol building at the time of the insurrection, per the criminal complaint against Messer. Facebook told the FBI that the phone number provided by AT&T was linked to Messer’s Facebook account, where he posted several selfies from inside the Capitol during the riot.
Google gave the FBI precise location data showing Messer’s journey from Ohio to DC and back again between January 5 and 7, as well as his location on the afternoon of January 6 as he wandered around and ultimately inside the Capitol building. The complaint also lists videos of the riot posted on Messer’s YouTube channel, Messer’s YouTube searches, internet searches, and emails from his Gmail account — all used to help build a case against him.
Messer was arrested in late July. He has pleaded not guilty to charges including trespassing and violent entry on Capitol grounds.

This case is just a small part of what’s become one of the largest investigations in FBI history, as agents and other law enforcement officers scramble to identify hundreds, if not thousands, of people who invaded the Capitol on January 6 in an unprecedented attempt to stop the democratic transfer of power.
A year later and with more than 700 people charged, we now have a look at how the law enforcement agency handles such an enormous task (or at least, as much as they’re willing to reveal to the public). Rather than revealing the breadth of the FBI’s domestic surveillance capabilities, the majority of cases show the power of the tech industry to collect and collate vast amounts of data on its users — and their obligation to share that data with law enforcement when asked.
Case files on the hundreds of people arrested so far show a heavy reliance on the vast stores of data obtained from companies like Facebook and Google. Many defendants were identified simply by getting tips from the public. The FBI used its various social media accounts and a section of its website dedicated to the investigation to call for tips. The agency has received more than 200,000 of them, supplied by everyone from close family members to complete strangers. In some cases, amateur sleuths and crowdsourced investigations yielded better results faster than the professionals.
Even as the insurrection unfolded, it was apparent that there would be plenty of evidence for investigators to find if they wanted to pursue cases against the rioters. In fact, the rioters generated so much evidence that the Department of Justice has paid more than $6 million to build a database of it to provide to defendants’ attorneys as the cases wind their way through the legal system.
“I don’t think we can conclusively say that the social media evidence was the only thing that got them caught, but an element of social media evidence was involved,” Jon Lewis, research fellow at George Washington University’s Program on Extremism, told Recode. He added that social media evidence has played a role in about 75 percent of cases so far.
It’s now clear that the FBI either failed to recognize or neglected to act upon a threat that should have been hard to miss, if the agency had been thoroughly monitoring social media in the days leading up to the attack.
The FBI had to play catch-up
As the FBI’s investigation ramped up in the days and weeks following January 6, the agency found itself with images of thousands of potential suspects. To put names to faces, it appealed to the public for help, which has been quite effective. The FBI’s wanted posters have led to some of those 200,000 tips, while many others came from people who saw alleged participants’ own social media posts, read local media interviews with people who freely admitted to breaching the Capitol building, or even gotten confessions from matches on dating apps (this has happened at least twice on Bumble).
At the same time, loosely organized groups of online amateur sleuths, like the “Sedition Hunters,” have amassed their own pool of suspects. Sometimes, the sleuths find clearer photos than what the FBI has. They’ve also given them clever hashtags — #BloatedCuomo and #ZZTopPB, for instance — to help their photos circulate and be more memorable.

“In some ways, they kicked the FBI’s butt in the early days in terms of using these investigative techniques and open source intelligence to figure out who a lot of these individuals were,” said Ryan Reilly, senior justice reporter at HuffPost, who has been tracking the Sedition Hunters’ efforts for an upcoming book.
There is at least one case of the Sedition Hunters doing a better job of identifying a suspect than the FBI did. The FBI falsely identified an Alaska woman as a person who helped steal a laptop from House Speaker Nancy Pelosi’s office. Agents went so far as to break down the woman’s door and search her home last spring. But looking through Facebook and using publicly available facial recognition tools, online sleuths were able to identify another woman, Maryann Mooney-Rondon, as the suspect. They found photos of Mooney-Rondon wearing the same jewelry as the woman in the video inside the Capitol building. She and her son Rafael Rondon were arrested in October and pleaded not guilty to charges including theft of government property and trespassing.

The FBI might not have to rely so heavily on others to make these initial identifications if the alleged participants were on their radar in the first place. Despite having months, if not years, to recognize the growing threat of QAnon conspiracy theorists, white supremacists, and right-wing extremists, including the Proud Boys, the Oath Keepers, and the Three Percenters, the FBI failed to realize the potential for violence those groups could do.
They also didn’t seem to take seriously the widely publicized “Stop the Steal” rally that immediately preceded the insurrection and prompted thousands to march to the Capitol in an attempt to stop Joe Biden from becoming president. There was at least one FBI informant in the crowd, and reports about what law enforcement knew and when have varied. But many see January 6 as a fundamental failure to either collect or correctly assess intelligence (if not both), given the ultimate result.
“The FBI and Justice Department have long deprioritized white supremacist and far-right militant violence in their domestic terrorism program,” Michael German, a former FBI agent and current fellow with the Brennan Center for Justice’s liberty and national security program, told Recode. “So it would seem that this was the prime opportunity for the FBI to engage. But they chose not to.”
Contrast this apparent lack of action with reports of law enforcement’s close monitoring and infiltration of groups associated with left-leaning movements, such as in Portland, Oregon. The New York Times recently reported that activists involved in Portland protests against police violence were subject to “extensive surveillance operations” in the summer of 2020. The FBI is also famous for decades of history surveilling Black activists, and there are countless reports of law enforcement monitoring of Muslim communities for years following 9/11.

“So much of the organizing went on in places that the FBI would never be allowed to surveil (particularly under a Trump presidency),” explained Joseph Brown, a professor of political science at University of Massachusetts Boston. “The agency’s surveillance capabilities are very good, but they could never have been employed fully in this case.”
German, the former FBI agent, says he finds it troubling that so many allegedly violent participants remain unidentified. He expected the agency to make it a priority to find and arrest the most dangerous offenders as soon as possible. Instead, it appears that the FBI has gone after the low-hanging fruit — the people who essentially “told on themselves,” as Lewis, the extremism researcher, noted.
The numbers back up these claims. Of the more than 725 people who have been arrested for Capitol riot-related crimes, less than a third of them have been charged with assaulting or resisting law enforcement officers, and only 75 people have been charged with using a deadly or dangerous weapon or causing serious bodily injury to an officer. At least 350 people the FBI suspects committed violent acts on Capitol grounds remain unidentified, though it’s likely this list will grow, with as many as 2,000 people expected to be charged by the time the investigation concludes. Meanwhile, the Sedition Hunters have listed hundreds more in their own unofficial database.
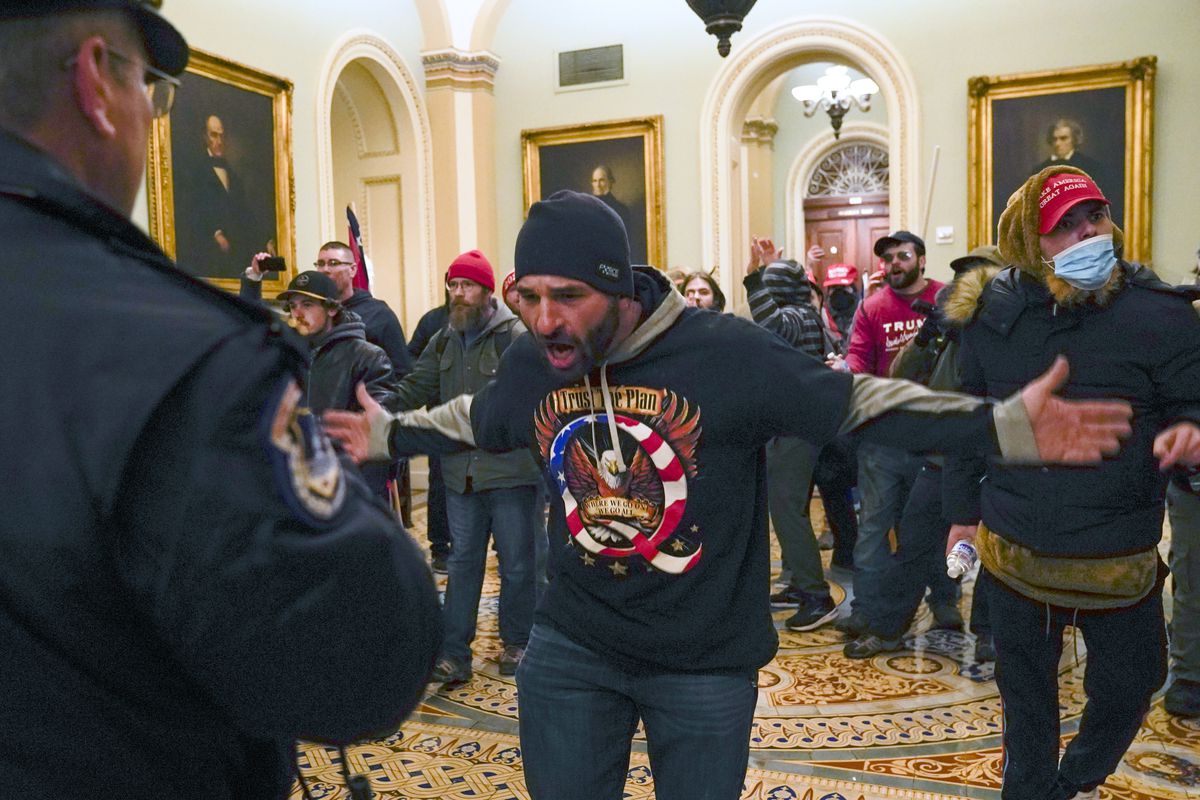
Data-hungry tech companies are making the FBI’s job easier
Reading through the cases of the people who have been charged paints a picture of just how extensively various companies track us, and how much more of our data a company like Google has than the actual government apparently does. The January 6 investigation is not an isolated example of this, although it makes for a pretty good one, given its scale, notoriety, and just how much digital evidence was left by so many people.
“Social media has become a place where investigators, more and more often, are getting formally trained to look for evidence … on a regular basis,” said Adam Wandt, professor at John Jay College of Criminal Justice and cybercrime investigations expert.
While those accused of taking part in the riot posted plenty of evidence on various platforms, tracking that goes on underneath the surface can also be used against them in the coming months and years. Though controversial, law enforcement has used some of these methods of tracking and data collection in the Capitol insurrection investigation.
For example, the FBI admits to using commercial facial recognition technology systems, including Vigilant Solutions and Clearview AI, which scrape the internet for photos, rather than relying on license photos and mugshots. Stephen Chase Randolph was identified by using an “open source facial recognition tool” that matched a photo of him on his girlfriend’s Instagram page. Randolph is accused of assaulting a police officer and rendering her unconscious. He has pleaded not guilty.

Geofence warrants are another tool that has drawn concern among privacy and civil rights groups. Also known as reverse search warrants, these orders require companies to provide all the accounts that were in a certain area at a certain time, in the hope that a suspect can be identified within that group. That means the devices of perfectly innocent people might be caught in, essentially, a digital dragnet. Law enforcement agencies are using them more and more with little oversight. Documents in multiple January 6 cases say the FBI has and is using geofence data of all devices on the Capitol grounds during the insurrection. Anyone inside the Capitol building who had an Android phone turned on or used a Google application during the riot was likely caught in the geofence warrant.
This seems to be how the agency found Amy Schubert. After receiving a tip that a woman wearing a jacket with a Joliet, Illinois, union’s logo on it could be seen in a YouTube video of the insurrection, the FBI searched its geofence database for Google accounts that had a Joliet area code. There were six. Two of those belonged to women, and a quick search revealed Schubert’s Facebook page, which featured a photo of a woman who looked just like the woman in the video. Investigators got a search warrant for Schubert’s Google account and found that her phone was inside the Capitol building on January 6 and that it took several photos and videos while there. Some of them showed her husband, John. He was also arrested. Both Schuberts pleaded guilty to demonstrating in a Capitol building in December.

That’s not to say that the Schuberts and other Capitol rioters wouldn’t have been caught if not for Google; the FBI may have other tools at its disposal it could have used to identify and catch them. But Google certainly seems to be the simplest, and bound by the fewest legal restrictions when it comes to collecting and keeping so much data on so many people — unlike the government, which has to get warrants and show cause to monitor American citizens this way. That means a bunch of private businesses are almost certainly tracking you right now. Unless it has a good reason to do so, the government probably isn’t.
While tech companies have helped the FBI find the people who didn’t make much or enough of an effort to hide their actions, one of the most potentially dangerous suspects remains at large: The person who placed pipe bombs outside the Republican National Committee and Democratic National Committee headquarters the night before the insurrection has yet to be identified. The FBI is offering a $100,000 reward for information leading to an arrest, and has released surveillance videos and photos of the suspect with their face obscured, a map of their likely route, and detailed information about the shoes they were wearing.
The FBI also says it’s interviewed hundreds of people, collected tens of thousands of video files, and followed up on more than 300 tips trying to find the pipe bomber, yet they remain unknown and on the loose as far as we know. The Sedition Hunters have even dedicated a section of their site to them. But without a preponderance of social media evidence and mobile device data, it seems to be a lot harder for the FBI to identify people who make efforts to stay hidden.
Others have been less careful. In the weeks after the Capitol riot, Walter Messer, the Ohio man, did some internet sleuthing of his own, according to the web search history the FBI obtained from Google. He looked up news articles about Capitol arrests, FBI billboards, and Brian Sicknick, a Capitol Police officer who died shortly after the riot. Messer also wanted to know what the penalties were for violating federal trespassing laws. A few months later, when he was charged with breaking federal trespassing laws, these searches were used as probable cause to arrest him.






