reader comments
105 with
Microsoft on Tuesday profiled software for sale in online forums that makes it easy for criminals to deploy phishing campaigns that successfully compromise accounts, even when they’re protected by the most common form of multi-factor authentication.
The phishing kit is the engine that’s powering more than 1 million malicious emails each day, researchers with the Microsoft Threat Intelligence team said. The software, which sells for $300 for a standard version and $1,000 for VIP users, offers a variety of advanced features for streamlining the deployment of phishing campaigns and increasing their chances of bypassing anti-phishing defenses.
One of the most salient features is the built-in ability to bypass some forms of multi-factor authentication. Also known as MFA, two-factor authentication, or 2FA, this protection requires account holders to prove their identity not only with a password but also by using something only they own (such as a security key or authenticator app) or something only they are (such as a fingerprint or facial scan). MFA has become a major defense against account takeovers because the theft of a password alone isn’t sufficient for an attacker to gain control.
MFA’s Achilles’ heel: TOTPs
The effectiveness of MFA hasn’t gone unnoticed by phishers. Several campaigns that have come to light in recent months have underscored the vulnerability of MFA systems that use TOTPs, short for time-based one-time passwords, which are generated by authenticator apps. One campaign uncovered by Microsoft targeted more than 10,000 organizations over a 10-month span. The other successfully breached the network of security firm Twilio. Like the phishing kit Microsoft detailed on Tuesday, the two campaigns above used a technique known as AitM, short for adversary in the middle. It works by placing a phishing site between the targeted user and the site the user is trying to log in to. When the user enters the password into the fake site, the fake site relays it to the real site in real time. If the real site responds with a prompt for a TOTP, the fake site receives the prompt and passes it back to the target, also in real time. When the target enters the TOTP into the fake site, the fake site sends it to the real site.
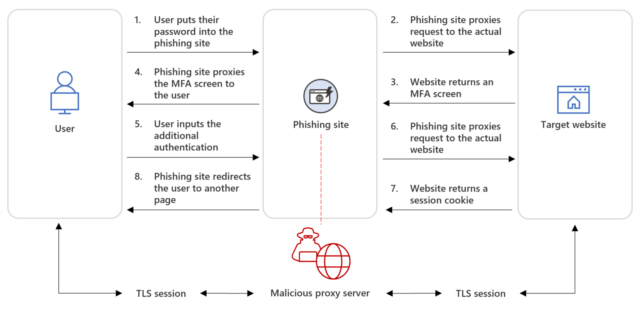
To ensure that the TOTP is entered within the time limit (usually about 30 seconds), the phishers use bots based on Telegram or other real-time messengers that automatically enter credentials quickly. Once the process is completed, the real site sends an authentication cookie to the fake site. With that, the phishers have everything they need to take over the account.
here, here, and here.
The phishing attack that breached Twilio’s network worked because one of the targeted employees entered an authenticator-generated TOTP into the attacker’s fake login site. The same campaign failed against content delivery network Cloudflare because the company used FIDO2-based MFA.