
When people ask me for security tips, I give them the basics. One is a strong and long password with upper and lower case letters, numbers, and special characters. (No, “Passw0rd!” is not good enough.) Each password should also be unique to each account (We love a good password manager!). And you always use two-factor authentication, or 2FA. (Don’t be like me, who didn’t have 2FA on her bank account until a hacker wired $13,000 out of it.) But the type of 2FA you use is also increasingly important.
Text-based 2FA, where a text with a six-digit code is sent to your phone to verify your identity, is better known and better understood because it uses technology most of us use all the time anyway. But it’s a technology that wasn’t meant to serve as an identify verifier, and it’s an increasingly insecure option as hackers continue to find ways to exploit it.
That’s why I recommend using an authenticator app, like Google Authenticator, instead. Don’t let the name intimidate you: There are a few extra steps involved, but the effort is worth it.
SIMjacking: Why your phone number isn’t good enough to verify your identity
By the time Mykal Burns got the security text from T-Mobile informing him that his SIM card had been changed to a different phone, it was already too late. In the 20 minutes it took Burns to get the SIM switched back to his phone, his Instagram account was gone. With access to Burns’s SIM card, the hacker simply asked Instagram to send Burns a password recovery text in order to take over Burns’s account and lock him out. All Burns could do was watch the hacker destroy that part of his online life.
“It had been wiped clean of the 1,200 or so photos I had shared since creating the account in 2012,” Burns, a Los Angeles-based television producer, told Recode.
SIMjacking, or SIM swapping, was famously used to take over Twitter co-founder and CEO Jack Dorsey’s own Twitter account in 2019. But as Burns’s story shows, you don’t have to be a famous billionaire to be a target. If a hacker knows enough about you to convince your mobile carrier that they are you, an unsuspecting customer service representative might switch your SIM to them. There have also been cases of mobile carrier employees accepting bribes to switch SIMs, in which case a hacker wouldn’t have to know much about you at all.
Putting a PIN on your SIM might prevent some of this, but it’s not foolproof. And, as Vice reported in March, hackers have found other SMS exploits that don’t even require access to your SIM card.
“SMS, as a technology, has been around for a long time,” Marc Rogers, executive director of cybersecurity at Okta, an identity authentication technology company, told Recode. “It was designed to be a cheap way of sending messages. It wasn’t designed to be secure. And we built a bunch of security services on top of it. … There are now more ways to compromise an SMS service than they can hope to fix.”
Basically, if you’re using texts or your phone number to verify your identity, it’s time to consider something else.
Authenticator apps — which are usually free — take a few more steps to set up than text-based authentication. Some people might find that — choosing and downloading another app, scanning QR codes, accepting tokens — to be too intimidating or simply not worth the extra effort. I’m here to tell you that it’s not intimidating, and it is worth it.
“That’s our whole purpose of really promoting these authentication apps,” Akhil Talwar, director of product management for LastPass, which makes a password manager and an authenticator app, told Recode. “They’re really easy to use, they’re super secure, and they’re also convenient. You’re just getting a push notification in some cases.”
How to choose and use an authenticator app
Authenticator apps work the same way text-based 2FA does, but instead of having a code sent to you via text, the code appears in the app. The code also changes every 30 seconds or so as an added measure of protection — it’s next to impossible for a hacker to guess at the right code when it changes so frequently. A hacker would have to be ridiculously lucky (anything’s possible, I guess) or have possession of your physical device to gain access to the code.
Several sites have recommendations for good authenticator apps and their respective features, which should help you figure out which one works best for you. Google Authenticator is one of the most popular and it comes from Google, so you can trust that it’ll be around for a long time and that the company knows what it’s doing to keep the app secure. But it’s also one of the most basic authenticator apps out there. If you’re looking for a few more features, Authy is highly recommended by most, has a nice interface, and lets you search within the app for a specific account (very helpful if you have a lot of accounts to scroll through), and is easier to switch to a new device than Google Authenticator. LastPass and 1Password’s authenticator apps can be linked to those companies’ password managers. And Microsoft’s authenticator — which, like Google, has the backing of a massive and long-running company behind it — is also a good choice.
“Three key things to think about when deciding on an authenticator app are the reputation and stability of the company that created it, the independent security reviews performed on it, and the ability to backup and restore the application in case of a lost or stolen phone,” Mathew Newfield, chief security and infrastructure officer at Unisys, told Recode.
Some authenticators have a push function where you simply confirm you’re trying to log into a site rather than remember and enter a six-digit code. But not all authenticator apps do this, and not all websites and apps support that functionality — at least, not yet. Some apps give you an option to have a backup in the cloud or to use the app across multiple devices, which you might be happy to have if your phone (and, therefore, authenticator app on it) breaks or is lost. Some apps have a search function so you can find the app you’re trying to log into easily — pretty helpful if you have a long list of logins.
“The one overarching rule is any authentication app is better than none,” Rogers, of Okta, said.
Once you’ve decided on an authenticator app and downloaded it to your device, it’s time to add your accounts to it.
In honor of our friend Burns, let’s use Instagram’s app as an example of how to connect your authenticator app to an account:
Go to Settings > Security > Two-Factor Authentication > Authentication App
From there, Instagram will ask to open your authenticator app and add your Instagram account automatically to it. You’ll then see a 6 digit code on the app. Enter that code on Instagram and you’re all set.
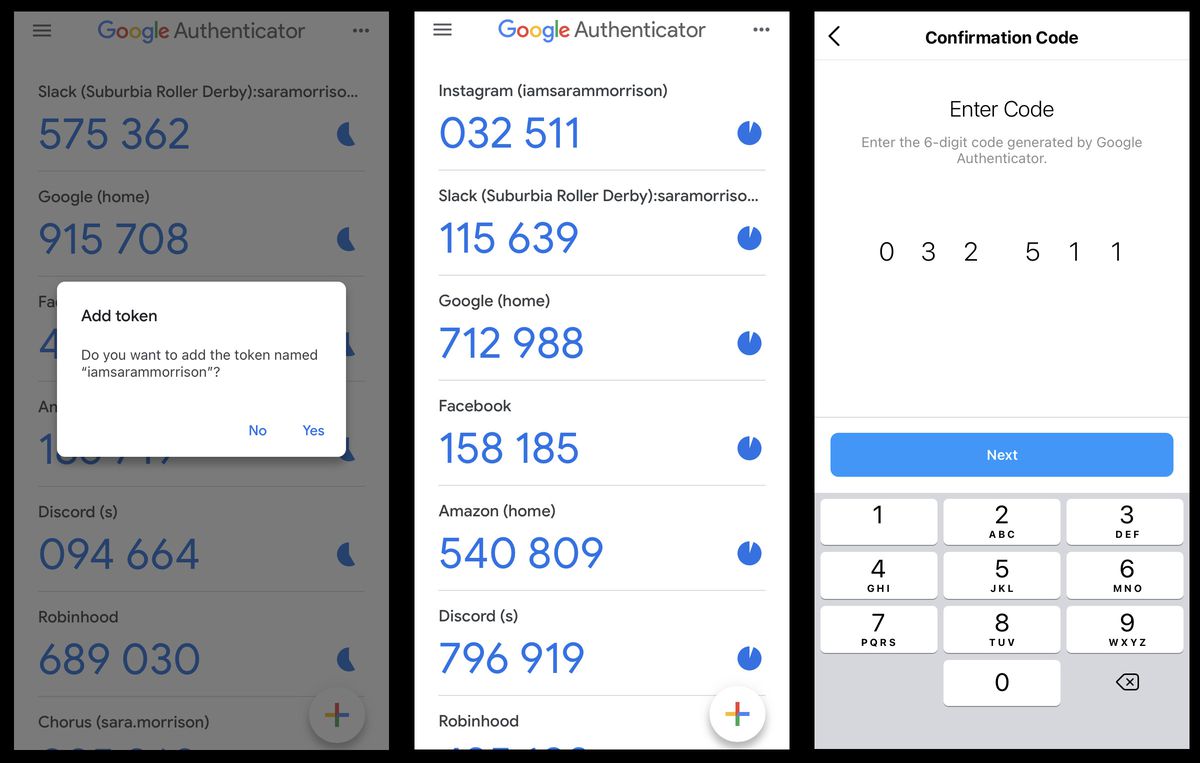
But you aren’t done. Instagram will then show you a set of backup codes. Write some or all of those down and keep them in a safe place (not on your phone) — you might need them to restore access to the app or website if you lose access to your phone and your authenticator app doesn’t have its own backup system.
Websites are a little different to set up. In honor of our other SIMjacked friend, Jack Dorsey, let’s use Twitter’s website as our example.
Go to Settings and privacy > Security and account access > Security > Two-factor authentication > Authentication app.
From there, you’ll be prompted to scan a QR code with your phone’s camera, which will open your authenticator app and add your Twitter account to it. If you can’t scan a QR code or the app won’t open correctly, you can also generate a code and enter it manually instead.
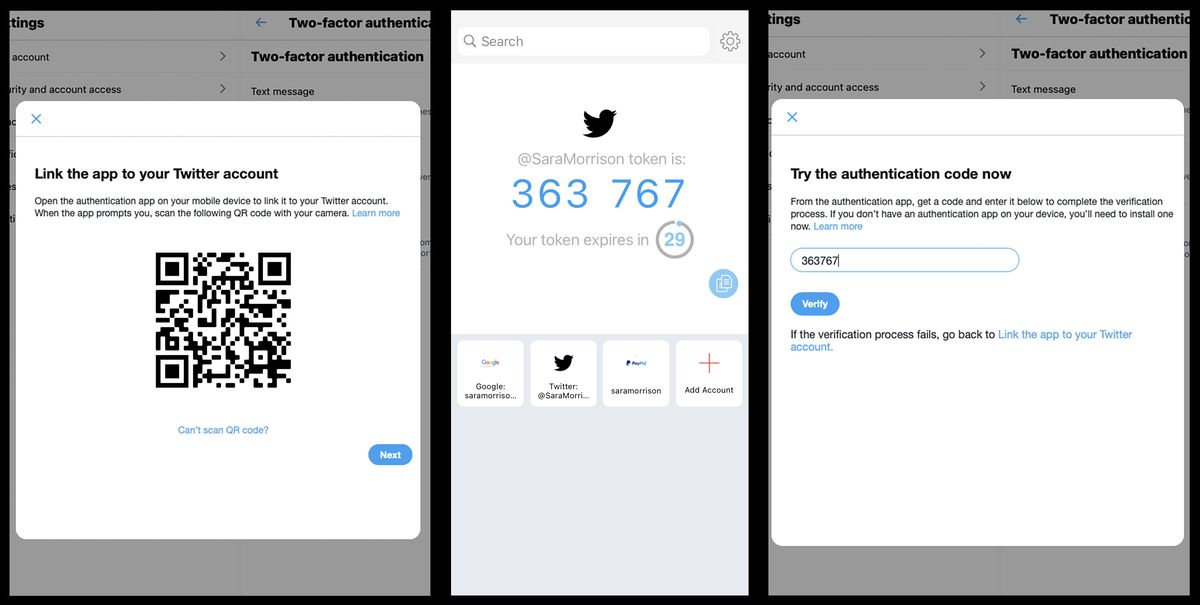
Back on Twitter’s site, click “next” and enter the six-digit code on your app. Again, remember to save Twitter’s backup code somewhere safe.
Now that you’re set up, when you log into Instagram or Twitter, you’ll be prompted to enter a code from your authenticator app. Open the app, get the code for the account you’re trying to log into, and enter that into the site or app. You can choose to do this every time you log into a site, or you can choose to only do it once if you’re using a device you trust. And that’s it.
Two very important and final things to remember
Once you’ve got the authenticator app up and running on an account, make sure you’ve disabled text-based 2FA and removed your phone number from the account (unfortunately, some apps and websites won’t let you do this). And don’t use your phone number as an account recovery backup option. After all, the whole reason why you’re doing this is that phone numbers make for poor identity verifiers.
Finally, if you’re getting a new phone, make sure you transfer your authenticator app from your old device to the new one. If your authenticator app requires that you have both devices in your possession to do this, make sure you plan ahead, or else you’ll have to rely on all those account backup codes to manually restore access to your accounts. Not good. Not fun. But still better than being hacked.
Again, this is going to be a little more work than relying on SMS-based 2FA, but think about what you stand to lose if your accounts are hacked. You may not realize how valuable some of those accounts — and the things on them — are until you lose them. Burns now uses an authenticator app wherever possible. He was able to get his Instagram account back after two days, thanks to a connection he had at Facebook. But he didn’t get back the 1,200 photos that were on his account — including those of his beloved dog, Bonnie, who died last year. His Instagram account is private now, and his use of it has been sparing.
“I have most of the original photos backed up from my phone, but gone are any photo edits (filters, etc.) I made in the app, whatever memories I attached in the captions, and any comments from others,” Burn said. “Pretty disappointing … I didn’t really post anything to the account for a year after getting it back, and have only recently begun posting photos again.”
Open Sourced is made possible by Omidyar Network. All Open Sourced content is editorially independent and produced by our journalists.






