reader comments
16 with 16 posters participating
Google’s Project Zero vulnerability research team detailed critical vulnerabilities Zoom patched last week making that made it possible for hackers to execute zero-click attacks that remotely ran malicious code on devices running the messaging software.
Tracked as CVE-2022-22786 and CVE-2022-22784, the vulnerabilities made it possible to perform attacks even when the victim took no action other than to have the client open. As detailed on Tuesday by Google Project Zero researcher Ivan Fratric, inconsistencies in how the Zoom client and Zoom servers parse XMPP messages made it possible to “smuggle” content in them that usually would be blocked. By combining those flaws with a glitch in the way Zoom’s code-signing verification works, Fratric achieved full code execution.
“User interaction is not required for a successful attack,” the researcher wrote. “The only ability an attacker needs is to be able to send messages to the victim over Zoom chat over XMPP protocol.” Fratric continued:
Initial vulnerability (labeled XMPP Stanza Smuggling) abuses parsing inconsistencies between XML parsers on Zoom’s client and server in order to be able to “smuggle” arbitrary XMPP stanzas to the victim client. From there, by sending a specially crafted control stanza, the attacker can force the victim client to connect to a malicious server, thus turning this primitive into a man-in-the-middle attack. Finally, by intercepting/modifying client update requests/responses, the victim client downloads and executes a malicious update, resulting in arbitrary code execution. A client downgrade attack is utilized to bypass signature check on the update installer. This attack has been demonstrated against the latest (5.9.3) client running on Windows 64-bit, however some or all parts of the chain are likely applicable to other platforms.
In December, Zoom finally joined the 21st century when it gave the macOS and Windows clients the ability to update automatically. The severity of the vulnerabilities fixed last week underscores the importance of auto update. Often, within a few hours or days of the updates like these becoming available, hackers have already reverse engineered them and use them as an exploit road map. And yet, one of the computers I regularly use for Zoom had yet to install the patches until Wednesday, when I thought to choose the “Check for Updates” option.
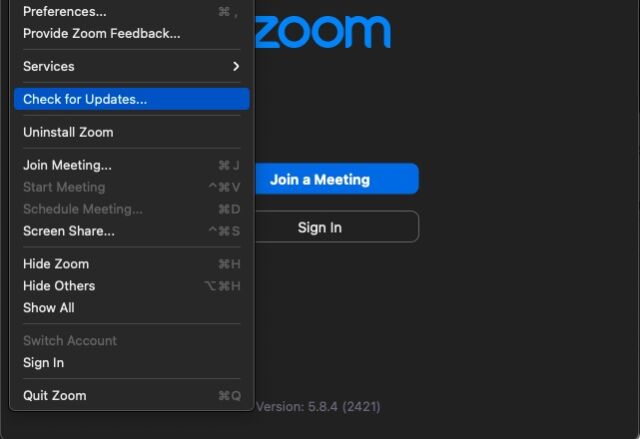
For my Zoom client to auto update, it needed to run an intermediate version first. Once I manually updated, the auto update was finally in place. Readers may want to check their systems to ensure they’re running the latest version, too.