Enlarge (credit: Drew Angerer | Getty Images)
(credit: Google)
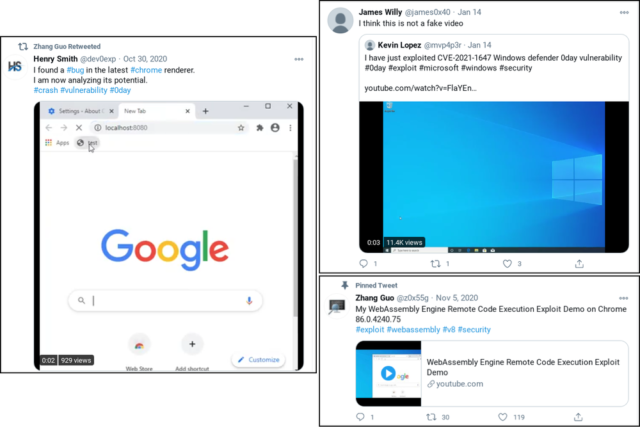
Eventually, the fake Twitter profiles asked the researchers to use Internet Explorer to open a webpage. Those who took the bait would find that their fully patched Windows 10 machine installed a malicious service and an in-memory backdoor that contacted a hacker-controlled server.
Read 6 remaining paragraphs | Comments