Composable enterprise spurs innovation
Overall, 74% of companies accelerated plans to move to the cloud by more than a year,…
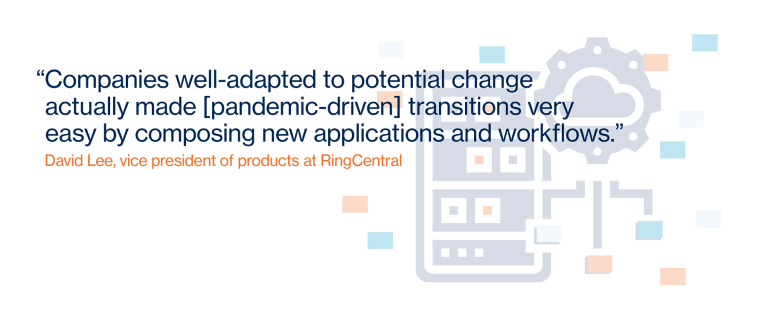
Overall, 74% of companies accelerated plans to move to the cloud by more than a year,…
Your daily activities might be substantially enhanced by current e-commerce technologies and tools. ERP and CRM…

reader comments 55 with 37 posters participating Share this story Chinese university students have been lured…

On a rainy Tuesday in June, I found myself in a packed and buzzing Times Square…
It wasn’t science that convinced Google engineer Blake Lemoine that one of the company’s AIs is…

Getty Images reader comments 1 with 1 posters participating Share this story In online crime forums,…
You can say a lot about the world of digital marketing, but you can’t say that…
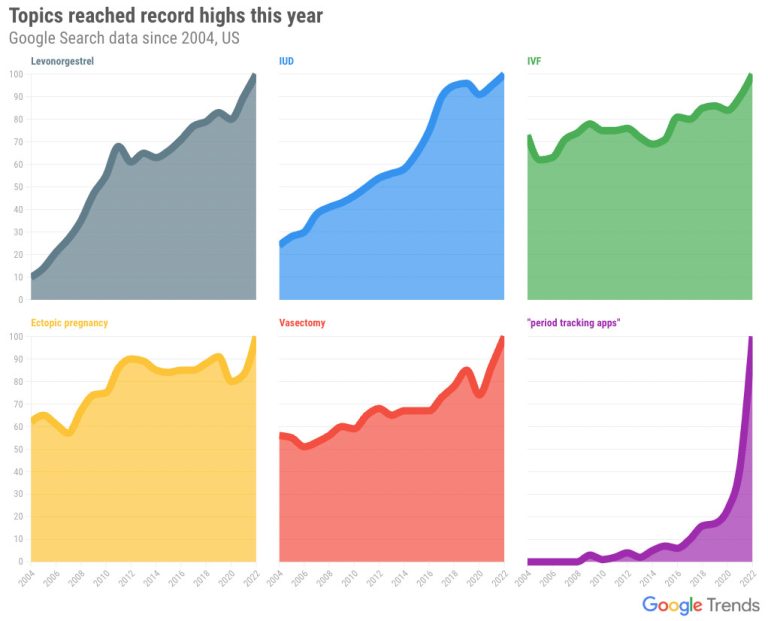
When the Supreme Court overturned Roe v. Wade last Friday, many Americans were upset and confused…

Spoiler alert: our annual Innovators Under 35 list isn’t actually about what a small group of…
Today, many companies use special technologies to improve the business of e-commerce. There are many extensions…

Alison Giordano just wanted to help out a friend, but instead, she almost lost her Instagram…

Firebear Improved Configurable Product for Magento 2 – Extension Change Log | FireBear Now compatible with…

Getty Images reader comments 149 with 95 posters participating, including story author Share this story An…

China has come to dominate the market in recent years, and by 2017 the country produced…

Enlarge / Drowning in a sea of data. reader comments 132 with 58 posters participating Share…