reader comments
44 with 0 posters participating
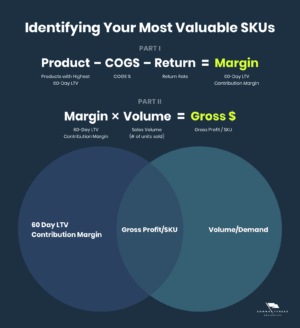
It is common to hear news reports about large data breaches, but what happens once your personal data is stolen? Our research shows that, like most legal commodities, stolen data products flow through a supply chain consisting of producers, wholesalers, and consumers. But this supply chain involves the interconnection of multiple criminal organizations operating in illicit underground marketplaces.
The stolen data supply chain begins with producers—hackers who exploit vulnerable systems and steal sensitive information such as credit card numbers, bank account information, and Social Security numbers. Next, the stolen data is advertised by wholesalers and distributors who sell the data. Finally, the data is purchased by consumers who use it to commit various forms of fraud, including fraudulent credit card transactions, identity theft, and phishing attacks.
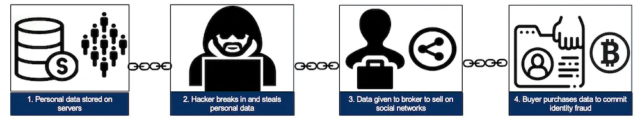
This trafficking of stolen data between producers, wholesalers, and consumers is enabled by darknet markets, which are websites that resemble ordinary e-commerce websites but are accessible only using special browsers or authorization codes.
We found several thousand vendors selling tens of thousands of stolen data products on 30 darknet markets. These vendors had more than $140 million in revenue over an eight-month period.
Darknet markets
Just like traditional e-commerce sites, darknet markets provide a platform for vendors to connect with potential buyers to facilitate transactions. Darknet markets, though, are notorious for the sale of illicit products. Another key distinction is that access to darknet markets requires the use of special software such as the Onion Router, or TOR, which provides security and anonymity.
Silk Road, which emerged in 2011, combined TOR and bitcoin to become the first known darknet market. The market was eventually seized in 2013, and the founder, Ross Ulbricht, was sentenced to two life sentences plus 40 years without the possibility of parole. Ulbricht’s hefty prison sentence did not appear to have the intended deterrent effect. Multiple markets emerged to fill the void and, in doing so, created a thriving ecosystem profiting from stolen personal data.
Christian Jordan Howell is assistant professor in cybercrime, University of South Florida, and David Maimon is professor of criminal justice and criminology, Georgia State University.
This article is republished from The Conversation under a Creative Commons license. Read the original article.