![iOS VPNs have leaked traffic for years, researcher claims [Updated]](https://whowillcare.net/wp-content/uploads/2022/08/ios-vpns-have-leaked-traffic-for-years-researcher-claims-updated.jpg)
reader comments
84 with 54 posters participating, including story author
(Update, Aug. 18, 2:40 p.m.: Proton founder and CEO Andy Yen said in a statement: “The fact that this is still an issue is disappointing to say the least. We first notified Apple privately of this issue two years ago. Apple declined to fix the issue, which is why we disclosed the vulnerability to protect the public. Millions of people’s security is in Apple’s hands, they are the only ones who can fix the issue, but given the lack of action for the past two years, we are not very optimistic Apple will do the right thing.”)
Original story: A security researcher says that Apple’s iOS devices don’t fully route all network traffic through VPNs as a user might expect, a potential security issue the device maker has known about for years.
Michael Horowitz, a longtime computer security blogger and researcher, puts it plainly—if contentiously—in a continually updated blog post. “VPNs on iOS are broken,” he says.
Any third-party VPN seems to work at first, giving the device a new IP address, DNS servers, and a tunnel for new traffic, Horowitz writes. But sessions and connections established before a VPN is activated do not terminate and, in Horowitz’s findings with advanced router logging, can still send data outside the VPN tunnel while it’s active.
In other words, you might expect a VPN client to kill existing connections before establishing a secure connection so they can be re-established inside the tunnel. But iOS VPNs can’t seem to do this, Horowitz says, a finding that is backed up by a similar report from May 2020.
“Data leaves the iOS device outside of the VPN tunnel,” Horowitz writes. “This is not a classic/legacy DNS leak, it is a data leak. I confirmed this using multiple types of VPN and software from multiple VPN providers. The latest version of iOS that I tested with is 15.6.”
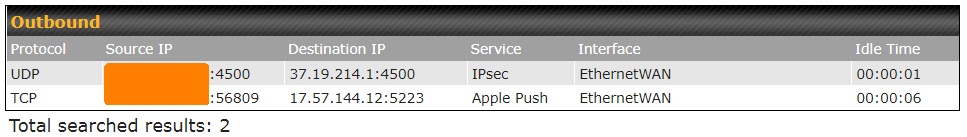
Privacy company Proton previously reported an iOS VPN bypass vulnerability that started at least in iOS 13.3.1. Like Horowitz’s post, ProtonVPN’s blog noted that a VPN typically closes all existing connections and reopens them inside a VPN tunnel, but that didn’t happen on iOS. Most existing connections will eventually end up inside the tunnel, but some, like Apple’s push notification service, can last for hours.
split tunneling,” focusing instead on the promise of a VPN capturing all network traffic. For his part, Horowitz recommends a $130 dedicated VPN router as a truly secure VPN solution.
VPNs, especially commercial offerings, continue to be a complicated piece of Internet security and privacy. Picking a “best VPN” has long been a challenge. VPNs can be brought down by vulnerabilities, unencrypted servers, greedy data brokers, or by being owned by Facebook.
(Update 2:58 pm ET: Updated to address notion of split tunneling and VPN expectations.)
(Update 12:53 pm ET, Aug. 25: Corrected a typo in a VPN company’s name. Ars regrets the error.)






