
Enlarge / Computer chip with Chinese flag, 3d conceptual illustration. (credit: Steve McDowell / Agefotostock)
Read 10 remaining paragraphs | Comments

Enlarge / Computer chip with Chinese flag, 3d conceptual illustration. (credit: Steve McDowell / Agefotostock)
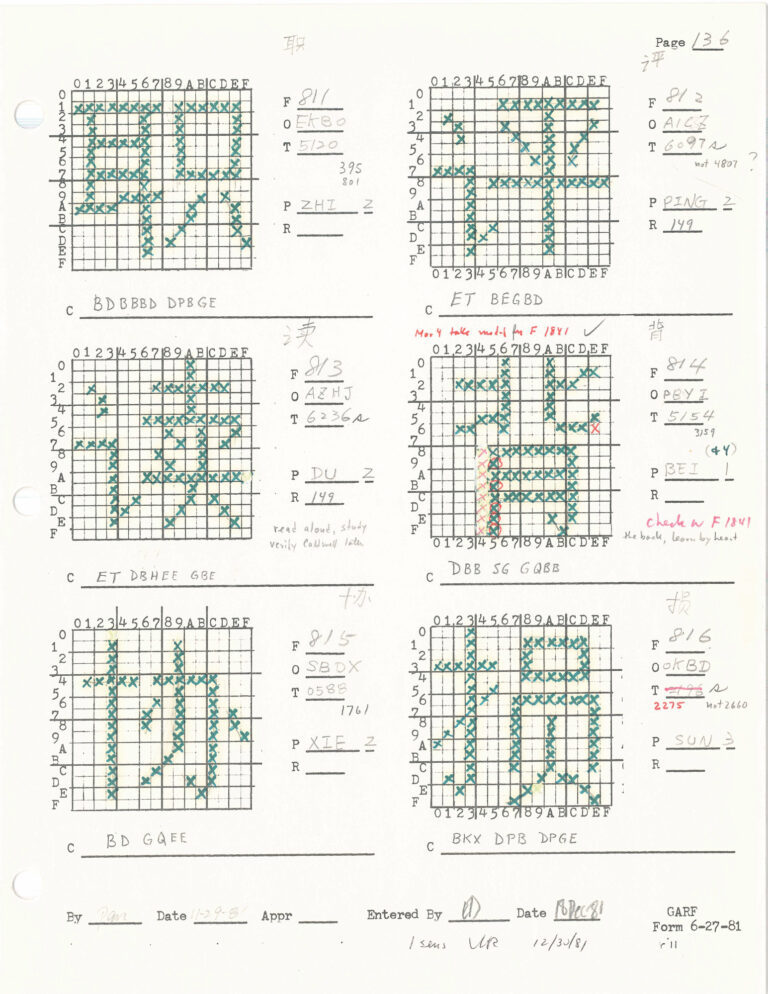
But there are tens of thousands of Chinese characters, and a 5-by-7 grid was too small…

Enlarge / This is definitely not a Razer mouse—but you get the idea. reader comments 82…

Is 2021 the year we’ll finally get a federal consumer privacy law? Barring another worldwide disaster,…

Una Brands’ co-founders (from left to right): Tobias Heusch, Kiren Tanna and Kushal Patel. Image Credits:…

Twitter thinks your tweets — or at least some of them — might actually be worth…

There are various e-commerce platforms that have specialized app shops. The same is true of BigCommerce….